Symantec researchers have found a loophole in how iPhone users pair devices with Mac workstations and laptops. They say attackers can exploit this flaw —which they named Trustjacking— to take over devices without the phone owner's knowledge.
At the technical level, the Trustjacking security issue is rooted in the "iTunes Wi-Fi sync" feature included with iTunes.
If this option is enabled in the iTunes settings section, when a Mac laptop/workstation owner syncs a new iPhone to his computer, this feature allows him to connect at any time to the smartphone via the local WiFi network, instead of using a wired cable.
The feature is convenient, and for solid reasons, as it allows a PC owner to easily retrieve or send data from the smartphone via the iTunes app and its API.
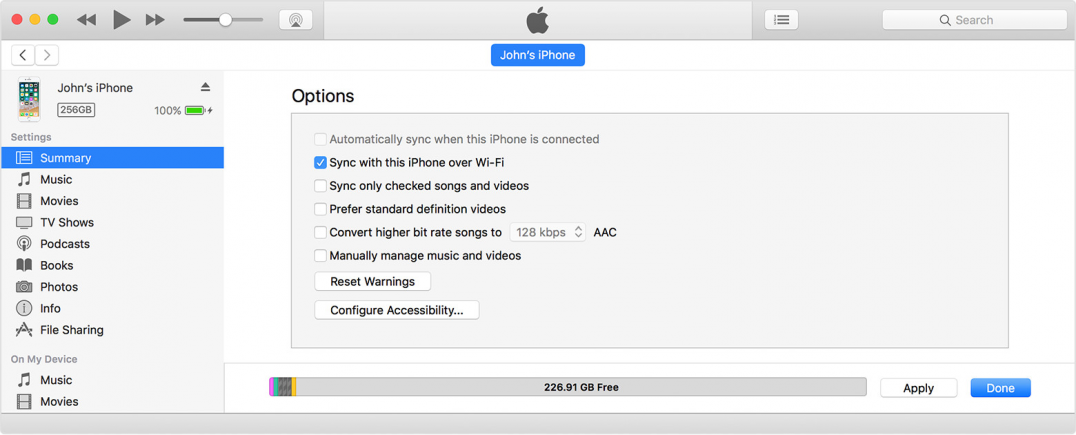
But Symantec researchers say there's a flaw in the design of this feature, which continues to grant a computer owner access to a paired iPhone via the local WiFi network, even after the iPhone device has disconnected from the computer.
Attackers can take control of iPhones via local WiFi
Presenting their findings today at the RSA 2018 security conference, Roy Iarchy, Head of Research and Modern OS Security at Symantec, says an attacker can abuse the iTunes Wi-Fi sync feature to take control of a device at later times, with no visible indicator to the device owner.
Iarchy says that once the iTunes WiFi sync feature is enabled, and a victim has been tricked into pairing with a malicious device, the attacker can use the iTunes API to record the user's smartphone screen by taking repeated screenshots at short intervals and sending the screenshots back to the iTunes app.
Furthermore, the attacker can also install or remove apps, all without any interaction with the iPhone owner, and can even trigger a remote backup, have it sent to his computer, and later sift through the victim's data.
Social engineering needed... and not needed
Obviously, such attacks aren't possible without social engineering, as the iPhone owner still needs to click on a popup that appears on his iPhone and agree to pair with an attacker's device.
You'd think this limits the attack surface only to situations where you're in a hurry and agree to pair your device with a stranger's laptop so that you can recharge your phone.
But the reality of Trustjacking attacks is different. Iarchy says that malware that infects your Mac laptop/workstation could enable the "iTunes WiFi sync" feature using automated scripts, and then retrieve data or infect any of the paired iPhones that are connected to the same WiFi network.
Further, the attack can work even across the Internet, not only via the local WiFi network, if the Mac computer is on the same VPN network as a paired iPhone.
Symantec says Trustjacking patch is not complete
Symantec says it notified Apple of the issue, but the solution Apple implemented to address the problem of Trustjacking attacks did not please its researchers.
The solution that Apple came up was to ask the iPhone user to enter the phone's passcode when pairing to a computer. This fix prevents random people from quickly grabbing your phone and pairing it to their own laptops.
But Symantec says this update made to iOS did not address the issue of iTunes WiFi sync being able to retrieve data from the device even after the user has disconnected from the paired computer, as the attacker could still use iTunes to silently connect to the smartphone if it's still in WiFi range.
"While we appreciate the mitigation that Apple has taken, we’d like to highlight that it does not address Trustjacking in an holistic manner. Once the user has chosen to trust the compromised computer, the rest of the exploit continues to work as described," Iarchy said today in a blog post.
"Unfortunately, there is no way to list all of the trusted computers and revoke access selectively," the expert added. "The best way to ensure that no unwanted computers are being trusted by your iOS device is to clean the trusted computers list by going to Settings > General > Reset > Reset Location & Privacy, now you will need to re-authorize all previously connected computers next time you are connecting your iOS device to each device."




0 Comments:
Post a Comment